Written by Mike Volk, Cyber Specialist at PSA Insurance & Financial Services
Effective cyber risk management involves every part of an organization. Cybersecurity policies guide employee behavior and shape culture. Cybersecurity training helps employees — from IT staff to administrative professionals to C-suite executives — understand and protect the organization from cyber threats. Technology helps enforce policies and provides essential defense and detection capabilities. But the success of any initiative on this scale — one that impacts the entire organization —will succeed or fail based on the vision and engagement of executive leadership.
Developing and implementing an effective cyber risk management strategy is a vital element of your business’ success. Yet, for many leaders interested in improving cyber risk management, getting started can be one of the hardest parts. One crucial aspect of this strategy is ensuring compliance with ISO 27001, a globally recognized standard for information security management systems. Adhering to ISO 27001 compliance not only helps in mitigating cyber risks but also establishes a structured approach to safeguarding sensitive information, enhancing your organization’s overall cybersecurity posture.
Today, I’ll provide foundational information on the nature of cyber risk. My goals is to help you and your Information Technology team be on the same page when discussing cyber risk and how it can potentially impact your business. Then, in an upcoming post, I’ll provide best practices you can follow to begin a cyber risk review, which will help you better understand your unique cyber exposures and aid in creating a high-level cyber risk profile for your organization.
What Is Cyber Risk?
Cyber risk is typically portrayed as a mysterious hacker hiding in the shadows, breaking into your network and infecting it with malware. In reality, your organization’s cyber risk is comprised of a variety of factors — some that are unique to your organization, and some that are pertinent to all businesses. The diagram below provides a simplified visual representation of a cyber risk equation that helps define cyber risk.
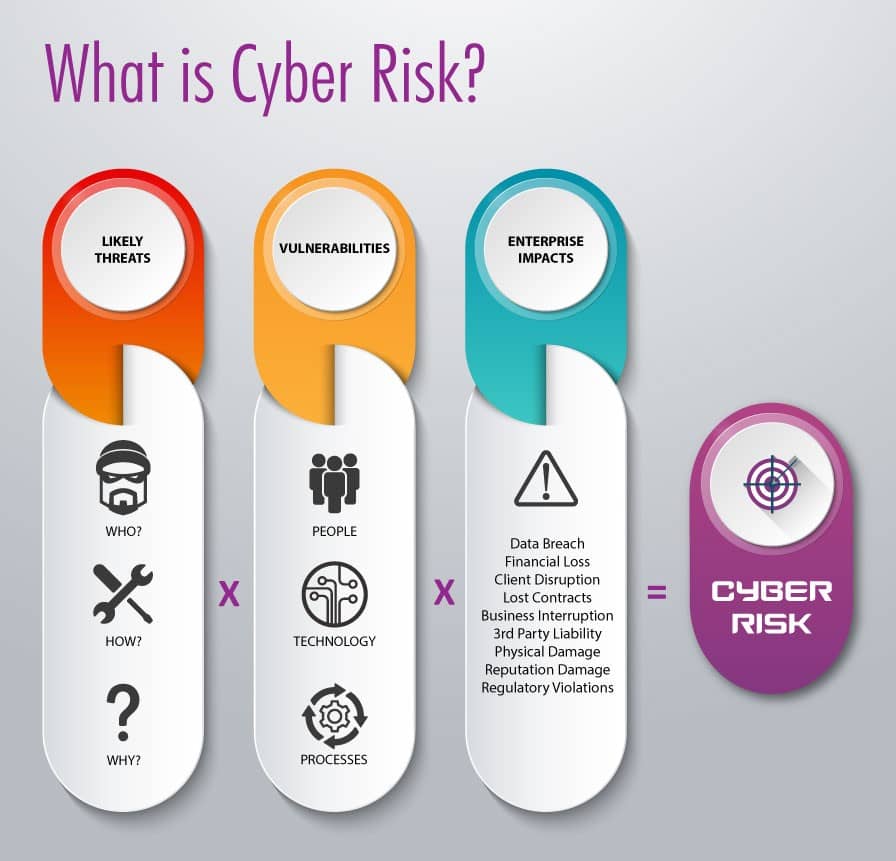
Figure 1. Cyber Risk Equation
Why Is Cyber Risk Different from Traditional Risk?
The complex nature of cyber risk makes it unique compared to traditional risks. For example, one familiar risk category for most organizations is their physical property. On any given day, it is possible that your property could be destroyed by a fire, flood, storm, vandalism or other incident. In this instance, there is a maximum loss value associated with the property, making the risk linear and relatively predictable based on historical data and other known factors.
In contrast, internet-connected technology creates a risk model that is fluid and unpredictable. By “plugging in,” each business, person, device becomes a node in a complex global system. In this system, cyber risk has the potential for exponential growth that is difficult to plot on a graph or predict with historical insurance models.
For example, if the network of an organization is infected with a virus, it is possible that the virus could damage the enterprise’s network and spread to every vendor, client, individual or other third party that is connected to the infected network. The virus may also allow a criminal to steal money or sensitive data, leading to other financial and legal implications for the business. Physical damage, such as a building burning down, could be devastating and may impact other nearby buildings. However, it is not possible for the fire to spread to the buildings of every third party that interacts with your business or lead to other unpredictable consequences like those a business might experience after a major data breach.
Effectively managing cyber risk is now a cost of doing business. It is important that decision makers begin building a baseline understanding of cyber risk, why it is challenging and how it impacts the organization. It’s also important to acknowledge that managing cyber risk is not free, and it requires a time commitment.
Smart leaders are beginning to understand this reality and are facing the challenge head-on. The good news is that with the right information and approach most leaders have the skills to guide the holistic cybersecurity strategy for their organization, even if they are not technical experts or directly involved in implementation. As a leader, simply placing an emphasis on cybersecurity as an enterprise priority is a good place to begin. Armed with a foundational understanding of cyber risk, a cyber risk profile specific to the organization, and the right internal team and external partners, every leader can help reduce risk and position the organization to be more resilient in today’s complex technology-driven environment.
In an upcoming blog post, we’ll outline the steps your organization can take to get started with a cyber risk review. In the meantime, if you have questions about how to increase your organization’s cyber resiliency, contact me at mvolk@psafinancial.com.
Information contained herein is generic in nature and provided by sources believed to be reliable. It is for informational purposes only and is not guaranteed as to accuracy, may not reflect our current opinion, and is not intended to replace the advice of a qualified professional. All rights reserved. No reproduction in whole or in part is permitted without the express written consent of PSA. PSA Insurance & Financial Services, its affiliates and employees are not responsible for the content of other web or social networking sites. PSA Financial Advisors, Inc. is a Registered Investment Advisory firm located at 11311 McCormick Road, Hunt Valley, MD 21031, and may only transact business in those states in which they are registered or exempted from registration. Contact our office at 410 821-7766. To protect your privacy, do not send personal information via the internet.

